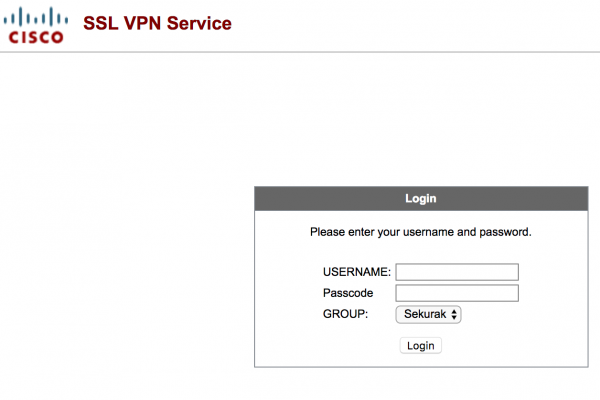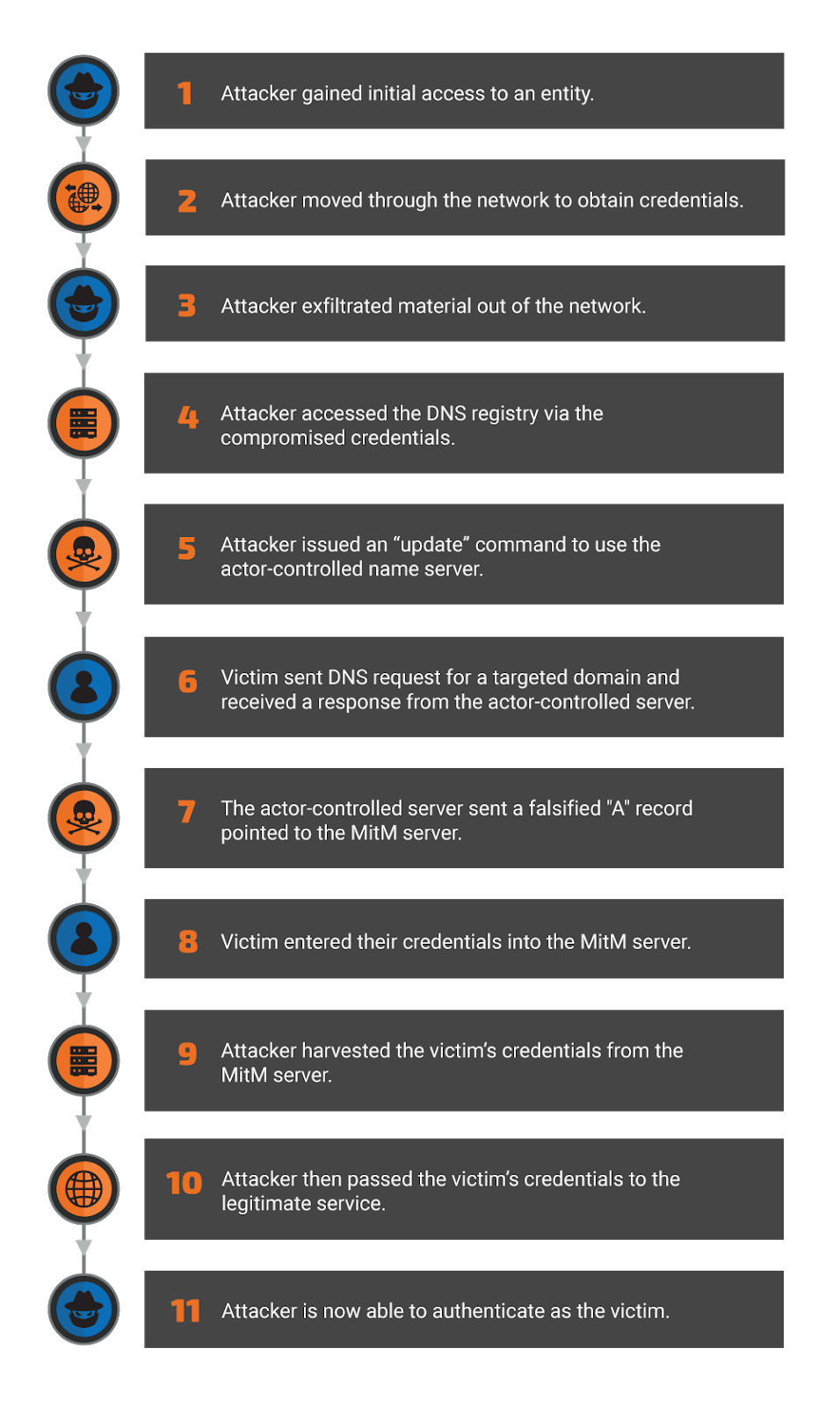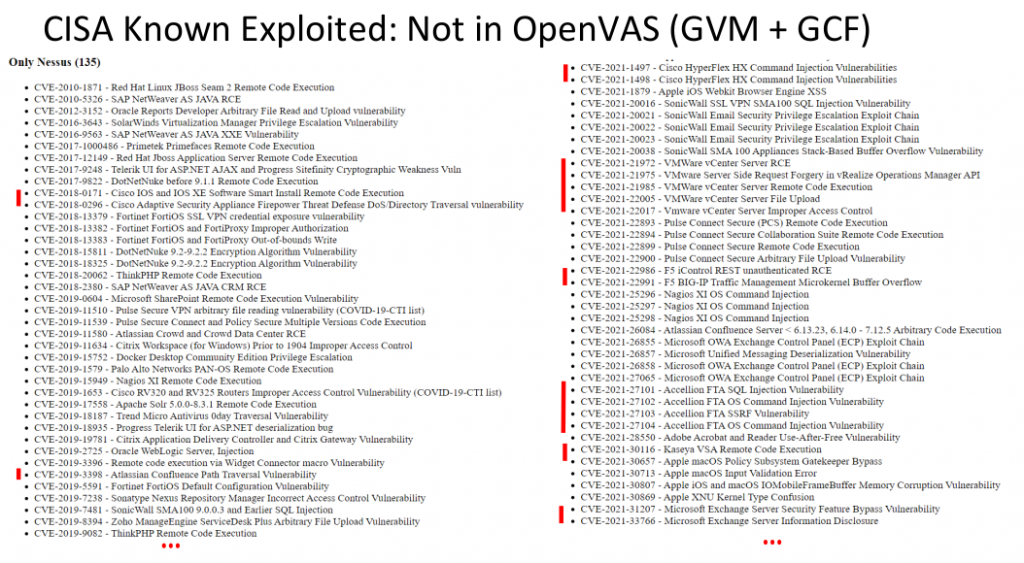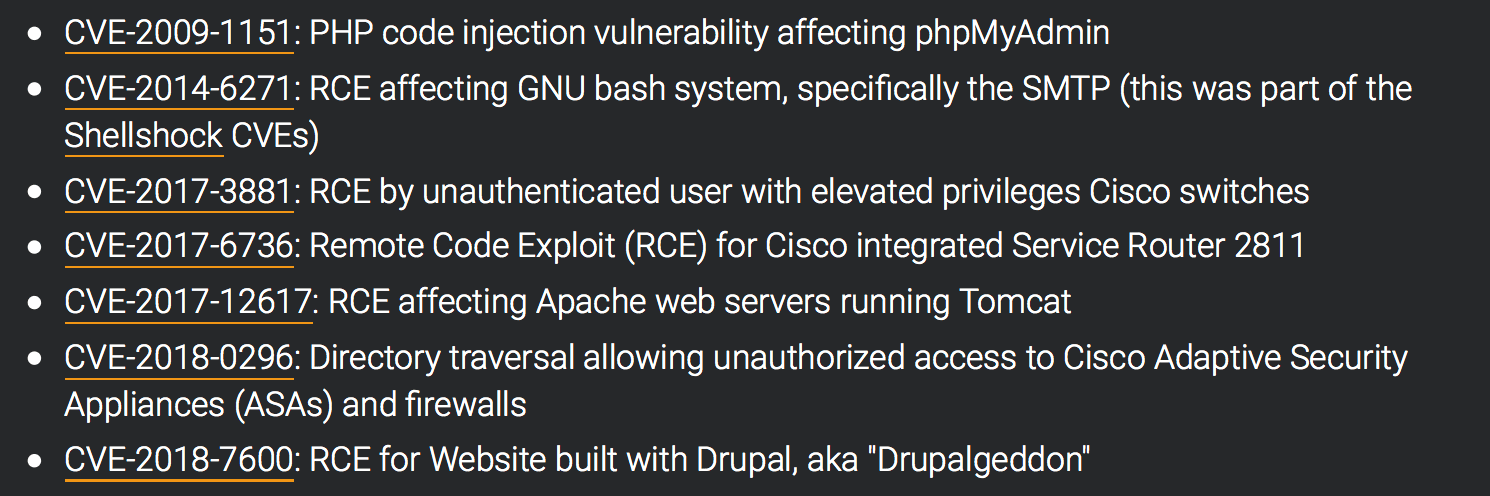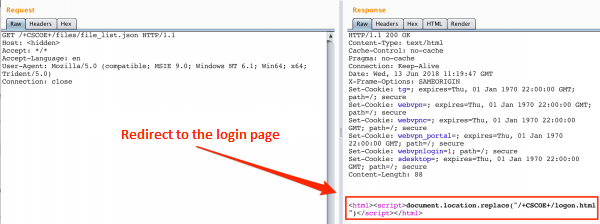
Description of CVE-2018-0296 vulnerability – bypassing authorization in Cisco ASA web interface. - research.securitum.com
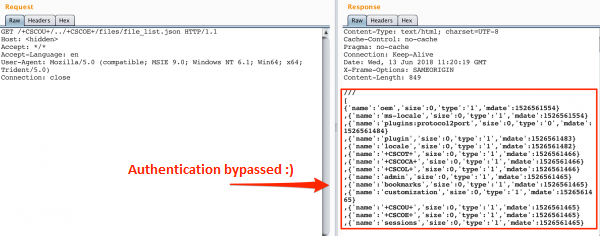
Description of CVE-2018-0296 vulnerability – bypassing authorization in Cisco ASA web interface. - research.securitum.com

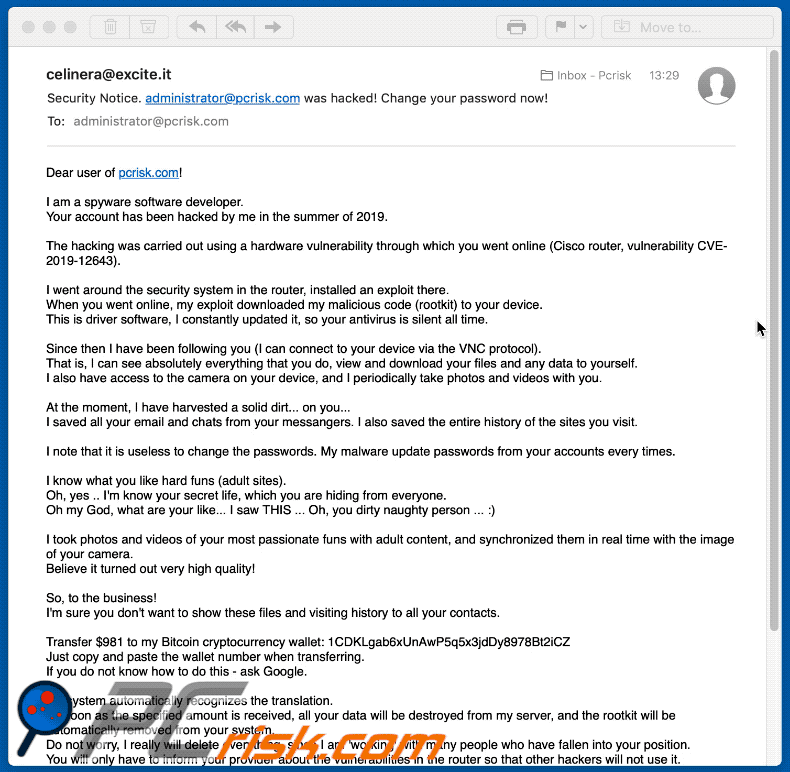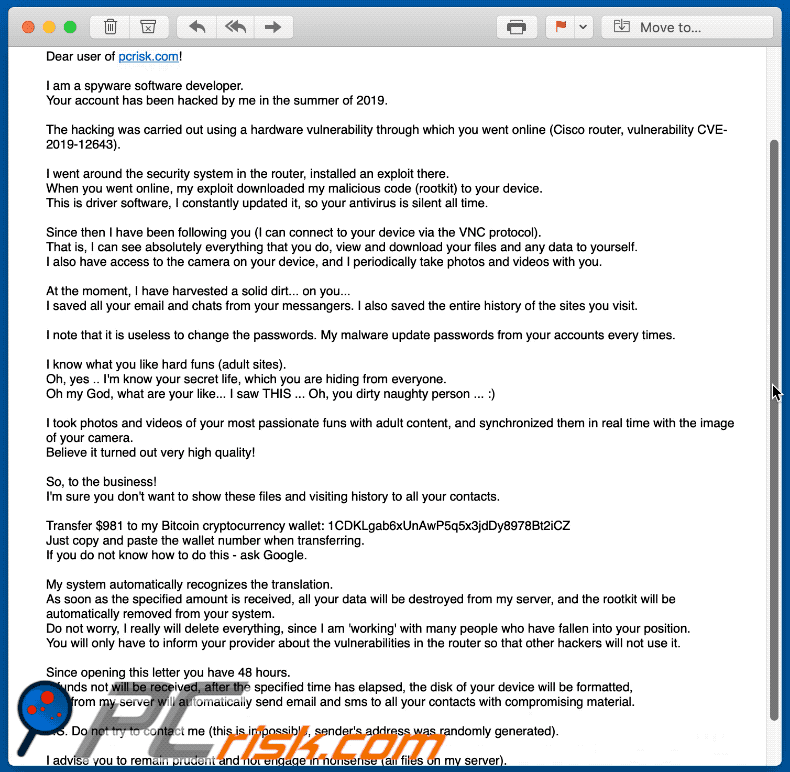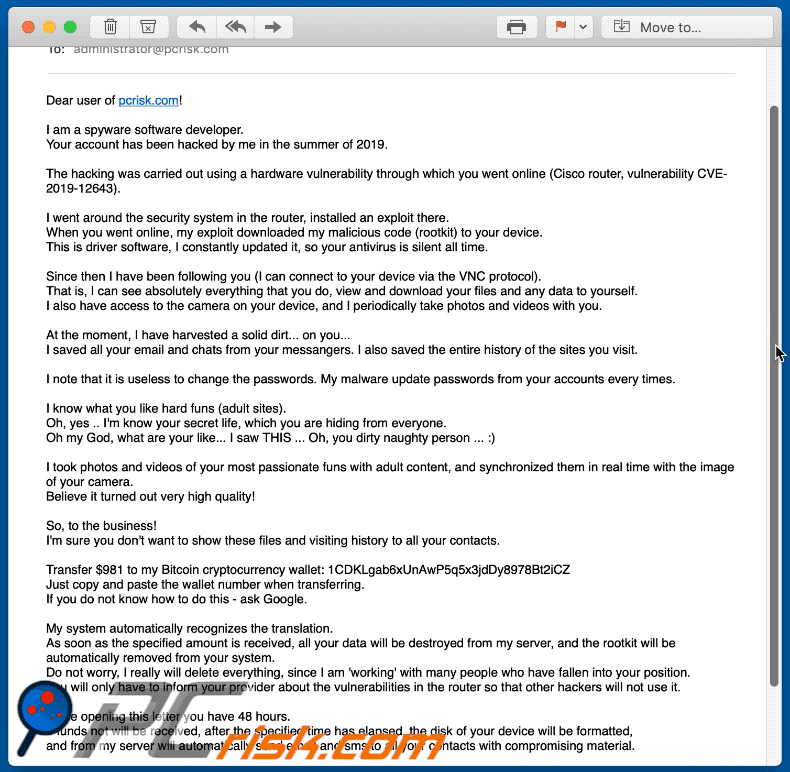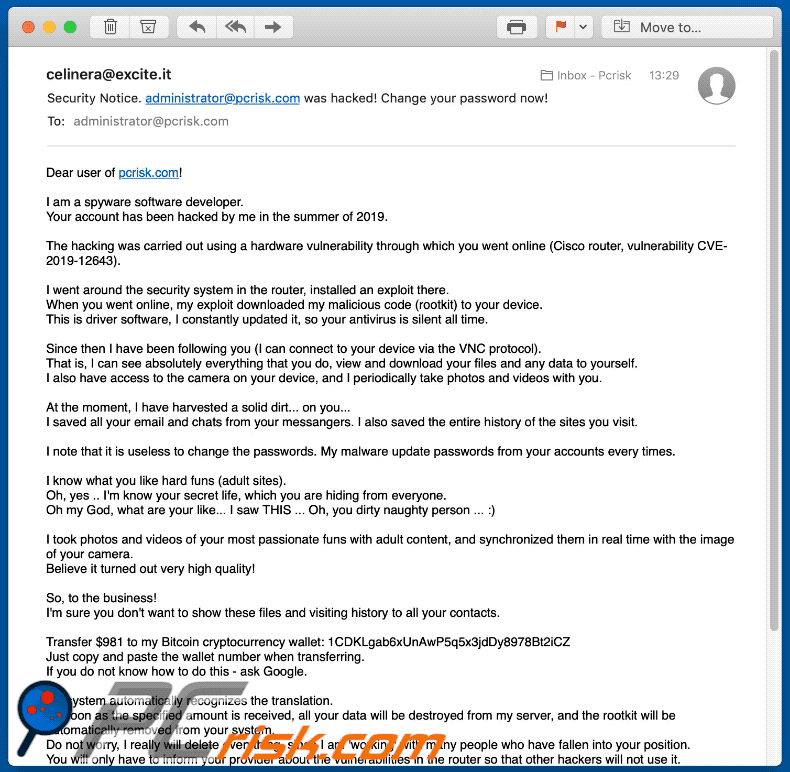
Have you received an email that demands ransom and claims to know your passwords? | ATUS | Western Washington University
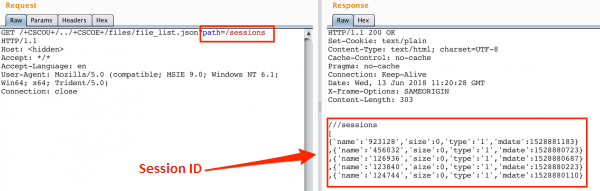
Description of CVE-2018-0296 vulnerability – bypassing authorization in Cisco ASA web interface. - research.securitum.com

Cisco PSIRT Notice About Public Exploitation of the Cisco ASA Web Services Denial of Service Vulnerability - Cisco Blogs